Global Site
Displaying present location in the site.
NEC’s Radio Identification Technology: Current Status and its Future
Sensing Technologies Underlying Social Systems: Sensing Technologies for Detection and RecognitionSensing technology has become ubiquitous and is now found almost everywhere, providing vast amounts of invaluable still and motion picture data. The mere presence of security cameras can deter crime, and analysis of still and video images from the scene can be useful in identifying, tracking down, and arresting a suspect. As sensing technology continues to proliferate, criminals are likely to respond by taking a more sophisticated approach such as exploiting blind spots and other weaknesses in video security systems. In the future, increased demand for new technology to supplement or replace conventional still and video imaging systems is expected. One of these potential new technologies ― radio identification ― is introduced in this paper. With radio identification, radio signals are collected by a radio sensor and analyzed to identify devices and users. In this paper, we will outline the component technologies of radio identification and examine some likely future use cases.
1. Introduction
Wireless devices such as smartphones have become a familiar ― and for some people an indispensable ― part of our daily lives. The fact that now almost everyone carries one of these wireless devices at all times makes them ideal for individual identification. Identify the device and you identify the person, making it possible to track suspicious people and sources of interfering waves.
One current tracking method uses media access control (MAC) addresses to identify individual wireless devices. It has, however, become a relatively simple matter to spoof MAC addresses and many smartphone models randomize MAC addresses, so this tracking method has limitations.
The radio identification system introduced in this paper bypasses this issue by identifying devices using the features extracted from the signal waveforms themselves. This means that counterfeit or randomized addresses cannot be used to outwit the system. Because this technology only applies to data in the physical layer and not the communications content, it offers a degree of protection for personal data that other systems do not.
2. Component Technologies of the Radio Identification System
2.1 Radio identification
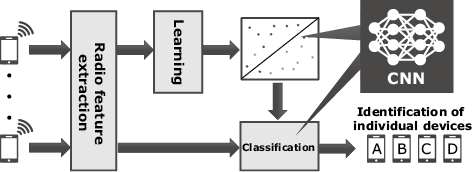
Radio identification is used to extract trivial device-specific differences as radio features from radio signals received by radio sensors, and these differences are generated by manufacturing variations in the analog circuits of wireless devices. These features are then classified using a pre-trained model to identify individual radio transmitters (Fig. 1). This is also called radio fingerprinting. In the following example (Fig. 2), these features are extracted from the IEEE 802.11g wireless LAN (WLAN) signals of two smartphones of the same model made by Company A. Although the positions of the peaks are similar, their heights are different. By focusing on such differences, this technology can accurately identify individual radio transmitters.

2.2 Power-spectral-density based radio features
Some previous studies assumed an environment in which signals could be detected with a sufficient signal-to-noise ratio (SNR) for identification, but the classification accuracy decreased in accordance with decreases in the SNR. In many cases, a dispersion of input data is generally assumed to be a Gaussian distribution in machine learning, and this makes effective learning easier. NEC has proposed the use of one-dimensional radio features to enable the distribution of data to be closer to that of a Gaussian distribution. As a result, an identification accuracy rate of 90% can be achieved when the SNR is 10 dB lower than that of the environment used in previous studies. This makes it possible to reduce the number of radio sensors needed to cover a given area by as much as 75%1).
2.3 Transmitter re-identification using radio features
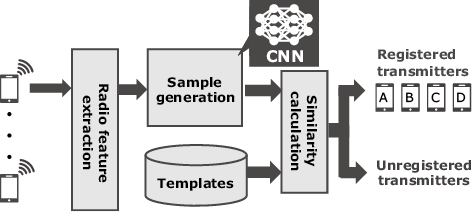
Radio identification often requires that a pre-trained learning model use a sufficient amount of transmission data collected from the identification targets. This is not a realistic situation, however, because it is not always possible to know what will be needed to obtain all possible signals from all transmitters for advance training. In NEC’s proposed method for transmitters’ re-identification (Fig. 3), signals that have not yet been learned are compared, using principles similar to those used in biometrics to identify faces and fingerprints. Specifically, the pre-trained model using a convolutional neural network is used to generate samples for re-identification (Fig. 1). By calculating the similarity between the generated samples and the templates registered in the database, this method can be used to determine if the transmitter has been registered, making it possible to re-identify even transmitters that have not been learned yet as long as templates for re-identification are registered in the database2).
2.4 Deep learning inference accelerator
To process radio identification in real-time, deep learning inference accelerators are required. These accelerators expected to reduce the system load and have recently become available at affordable prices. They consume significantly less power than a graphics processing unit (GPU) and could facilitate the creation of a more compact system. In most cases, however, they are often equipped with specific computing units for image processing, and this makes it impossible to use the one-dimensional features described in section 2.2. NEC solved this problem by including temporal information in the logarithmic power density and by generating two-dimensional features corresponding to images, and this made it possible to take advantage of an inference accelerator. As a result, NEC succeeded in reducing power consumption by 98% compared to when using a GPU. This is accompanied by a slight deterioration of about 2 dB in the SNR with an accuracy rate of 90%, and the discernible distance decreased by 12%3).
2.5 Future applications
NEC’s radio identification system can achieve excellence in an environment with limited differences between the learning signals and the inference signals in the vicinity of the radio sensor. Our tests have revealed, however, that performance degradation may be significant when fluctuation is considerably high in the sensor’s vicinity. NEC’s efforts in research and development (R&D) are now focusing on finding a solution for this issue.
While NEC’s R&D is currently aimed at WLAN devices such as smartphones, we are confident that this system can also be applied to the radio wave monitoring of problematic or illegal wireless stations and thereby identify the source of radio signals that interfere with critical wireless communications such as fire and disaster management radio communications, aeronautical radio communications, and more.
3. Overview of NEC’s Radio Sensor
To extract feature values from a radio signal, radio signals must be collected using a sensor. This sensor must meet a variety of criteria in terms of functions, performance, and structure. Radio signals can, for example, be collected by low-priced software defined radio (SDR) applications available on the market. In this section, the sensor that is currently under development and expected to improve radio-identification performance is discussed.
3.1 Features
The main features of the sensor NEC is now developing are as follows.
- Compatible frequencies: 20 MHz to 4 GHz
- Instantaneous reception bandwidth: 40 MHz (per channel)
- Dynamic range: 70 dB or more
- Number of reception channels: 8 channels (simutaneous reception possible)
- Power consumption: 70 W or less
- With pre-filter: For high electric field resistance
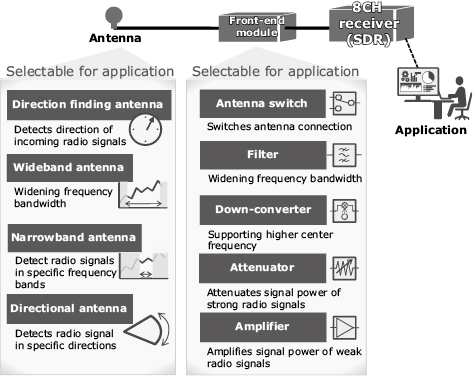
This sensor is also designed to allow for possible customization in accordance with the customer’s intended usage. Various combinations of antenna, front-end module, and application are possible (Fig. 4). NEC also offers an application programming interface (API) to facilitate introduction of this sensor to existing systems and development of related applications.
3.2 Applications
Because this sensor has simultaneous reception with a bandwidth of 40 MHz and eight channels, it can collect signals from and then identify multiple WLAN channels. With a wideband capability of eight channels and 40 MHz width per channel, this system can easily handle various communication frequencies, helping to prevent any features from eluding extraction.
Thanks to the dynamic range performance and to the pre-filter for a high resistance to electric fields, saturation is less likely to occur even in urban areas where radio signals are constantly being emitted. As a result, this sensor does not have any restrictions on where it can be used.
4. Usage
One use of radio identification might be the tracking of specific smartphone users. As shown by this conceptual diagram (Fig. 5), when the features extracted from the signals are received by the radio sensor and match the preregistered features when re-identified, the system operators are automatically notified so that the target’s specific whereabouts can be determined in real time. In addition to real-time specification and notification, captured radio signals can be stored for post hoc analyses.
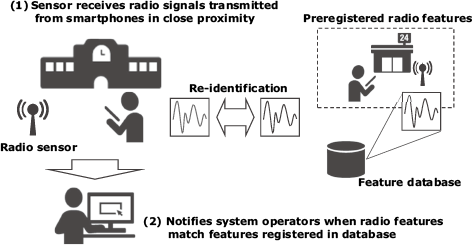
The protection of privacy, however, is an important consideration when handling collected radio features.
5. Use Cases
Here are some use cases for the radio identification system in various situations.
5.1 Searches for missing people
When people go missing, a search for them can be conducted by tracking the radio signals from their smartphone. Radio identification is expected to become an important additional tool in such searches, supplementing conventional methods such as witness interviews and analysis of security camera images. Even if the missing people change their appearance, such as their clothing, or even if they are indoors, radio signal sensors can still collect and identify radio signals as long as the missing people have their smartphones with them. In such cases, the effectiveness of tracking will be heightened by increasing the number of sensors installed on streets and in other public spaces in much the same way as security cameras are.
5.2 Prevention of continued stalking
Radio identification can be used to monitor convicted stalkers and prevent them from contacting their victims. Because round-the-clock protection for victims is problematic, the police have difficulty preventing stalkers from following and ambushing their prey. Radio identification enables the detection of radio signals from the stalker’s smartphone whenever the stalker approaches a circumscribed zone around the victim. Even if the stalker has not been identified, analysis of the time and the frequency of occurrence in which the sensor detects specific radio signals can make it possible to identify the suspect’s smartphone.
5.3 Detection of illegal radio signals
The sensor can detect communication devices that generate illegal radio signals which infringe upon laws such as Radio Act as well as the whereabouts of the device. Because the features of radio signals transmitted by the same model of a communication device will be similar from one device to the next, the presence of radio signals emitted from different individual devices can be detected if they are the same model. When used in combination with a function or a sensor that estimates the direction of the incoming waves, the source’s location can be identified. This can contribute to early detection and elimination of a communication device that may interfere in legitimate communications. Because the radio features must be preregistered in the system in accordance with the models that need to be detected, the features may need to be collected from confiscated illegal devices.
6. Conclusion
In this paper, various use cases for several different situations as well as component technologies of the radio identification system are discussed. We at NEC are now working to improve the system in various fading environment and are confident that once this is accomplished we will be able to apply the radio identification to a much wider range of use cases than discussed in this paper. While continuing to develop this system, we at NEC aim to create a safer city with our radio identification technologies.
Reference
- 1)Taichi Ohtsuji et al. :Noise-Tolerant, Deep-Learning-Based Radio Identification with Logarithmic Power Spectrum, ICC 2019 -2019 IEEE International Conference on Communications (ICC), 2019
- 2)Taichi Ohtsuji and Toshiki Takeuchi:Effect of learning patterns on radio re-identification using deep metric learning, Society Conference 2020, The Institute of Electronics, Information and Communication Engineers, 2020
- 3)Taichi Ohtsuji and Toshiki Takeuchi: A proposal of radio feature for inferring accelerator on deep-learning-based radio identification, Society Conference 2019, The Institute of Electronics, Information and Communication Engineers, 2019
Authors’ Profiles
Assistant Manager
Radio Application, Guidance and Electro-Optics Division
2nd Government and Public Solutions Division
Manager
Radio Application, Guidance and Electro-Optics Division
Principal Creator
System Platform Research Laboratories
Manager
2nd Government and Public Solutions Division

 PDF
PDF