Global Site
Displaying present location in the site.
NEC’s Online Personal Identification Service Accelerates Innovations Toward New Normal Era
In an unprecedented situation of the spread of COVID-19, various business types, business forms and services are being forced to change toward the New Normal. After the amendment entitled the Ordinance for Enforcement of the Japanese Act on Prevention of Transfer of Criminal Proceeds on Nov. 30, 2018, that would permit non-face-to-face personal identification, NEC Corporation began to provide an identification service making use of noncontact face recognition technology in 2019. It is expected that the use of digital technology would advance rapidly and the online identification service would play an important role in the world under/post COVID-19. This paper is intended to introduce the technology for implementing an online personal identification service matching the New Normal era and the enhancement of anti-impersonation measures.
1. Introduction
1.1 Online identity verification in the wake of COVID-19
The recent spread of COVID-19 is forcing various business types, business forms and services to change toward the New Normal state. Particularly, with business forms in which a person involved in the transaction is identified face to face, many of such businesses are transiting toward or expanding into online transactions. Nevertheless, transactions that fall outside laws and guidelines cannot be shifted quickly to such a new system.
In these circumstances, one can look to an industry that implemented online personal identification, also at the legal level, since before the spread of COVID-19. It is the financing institutions such as banks and securities firms. As the Japanese Act on Prevention of Transfer of Criminal Proceeds (hereafter referred to as Criminal Proceeds Act) forces financing institutions to enforce anti-money laundering measures in order to cut off money supplies to criminal organizations including drug dealers and terrorists, financing institutions need to verify personal identification of customers and the purpose of their transactions. These operations, featuring full personal identification, are generally called the KYC (Know Your Customer) process, and personal identification using an online means of verification is called the eKYC (electronic Know Your Customer) process. The use of eKYC in hastening the opening of an account and efficient checking of personal identification became active after the amendment on November 30th, 2018 of the Ordinance for Enforcement of the “Act” aiming at the use of online method for non-face-to-face personal identification. Its use is also spreading because of the need for quick personal identification by fund transfer business operators adopting cashless payment.
The eKYC is also expanding in other domains besides financing institutions. For example, it is used in cellphone purchase at communications carriers as prescribed by the Japanese Act for Identification, etc., by Mobile Voice Communications Carriers with their subscribers, etc., and for Prevention of Improper Use of Mobile Voice Communications Services. In the secondhand article purchase and rental industries, it is used for identification prescribed in the Japanese Act for Antique Dealing. Other use cases will be detailed later in this paper.
eKYC is also expected in other domains in the future, for example, in personal identification in online medical consultations.
While the COVID-19 virus was spreading actively, the existence of patients who were incapable of going to hospitals due to high risk of infection posed a problem. The Guidelines on the proper conduct of online medical consultations’ of the Japanese Ministry of Health, Labour and Welfare defines, “When a patient seeking online medical consultation transmits information on personal mental and physical status to the doctor, the doctor should show identification as a doctor and the patient should show identification as a patient to the other party. Even in online medical consultations, it is desirable to verify the patient by giving one’s full name in the same way as face-to-face examination.” For examples of specific ID documents, the guidelines say, “the doctor’s license can be verified by presenting the HPKI (Healthcare Public Key Infrastructure) card or medical license. At the same time the patient’s personal identity can be verified by presenting the “My Number card”.” The same approach is also going to be taken in the drug administration guidance by dispensaries. Smooth information linkage between online medical consultations and administration makes it possible to have secured care at home.
The use of online means is also under study in fields other than medicine, such as in the updating of various certificates. The targets are periodically-updated cards including driver’s license, My Number card, health insurance card and other qualification cards. This can be one of the COVID-19 countermeasures that reduces congestion thanks to elimination of the necessity of visiting offices.
1.2 Technical elements for eKYC implementation
The more the need for personal identification increases, the more the need for various identification techniques will increase.
One of the most basic identification methods is to read correctly the information on a certificate. Optical character recognition (OCR) using AI is the recently employed method. The readout using visible light is also effective. The next method is to match the face photo on the certificate with the face image of the person being identified, and the latest face recognition is effective with this method. It is also important to verify if the person presenting an ID card such as ID-Selfie is the person described on it. Also, the recent increase in certificates incorporating IC chips also make verification based on the information in the chip possible. The technologies to be combined and the depth of verification should conform to the applicable laws and agency guidelines. The details of each technology will be described later in this paper.
2. eKYC Implementation Technology
2.1 Outline of amendment of the Criminal Proceeds Act
The personal identification methods that are acceptable for completion online by the amendment of the Criminal Proceeds Act include the following four methods (Fig. 1). With the Digital KYC, NEC’s newly provided compatibility with a method based on matching with IC chip (Article 6, Paragraph 1, (i) (f)) in addition to the method based on photo capturing of customer’s face (Article 6, Paragraph 1, (i), (e)). The coverage of ID documents begins with the My Number card, driver’s license and residence card. With “Article 6, Paragraph 1, Item 1, (i) (f)”, the smartphone conforming to the “Act” is limited to NFC-compatible models. However, verifying the e-signature of IC chip eliminates the need of for the specific business carrier of “visual thickness check” so the work efficiency can be improved. It can also help prevent rejection of an application due to inability to capture the thickness of ID document.
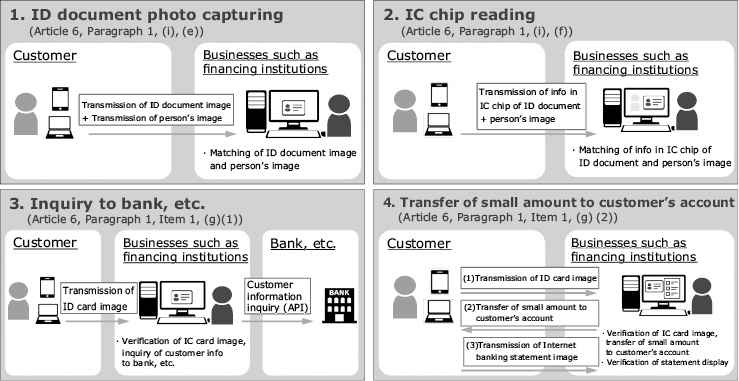
2.2 IC chip compatibility
The service for reading the IC chip in the personal ID document by smartphone has previously faced a bottleneck because the iPhone (iOS) used by many Japanese users did not have the necessary compatibility. However, opening of the NFC function to third parties in iOS13 released in September 2019 has made the service provision possible. As a result, both Android and iPhone terminals are capable of personal identification based on IC chip provided they are NFC compatible.
2.3 Outline of processing
The personal identification based on IC chip read-out takes the following flow (in the case when the My Number card is used).
2.3.1 OCR reading of card surface
The password for reading the face photo image and the four basic pieces of information (Identification number, B: 14-digit password including the date of birth + effective year + security code printed on the card surface that is generated automatically from the card surface info verification app or card surface info input assistance app in the IC chip. The automatically generated password is used to read the IC chip so locking due to unmatching of the manually-entered identification (locking after 10 times of unmatching) can be prevented (Fig. 2).

2.3.2 IC chip reading
The identification number B read from the card surface and generated in paragraph 2.3.1 is used to read the face photo with the card surface info verification app in the IC chip. The card surface info input assistance app reads the text required at the time of application for the desired procedures, such as the full name, address and date of birth. Absence of falsification of the data is confirmed by verifying the e-signature in the IC chip (Fig. 3).

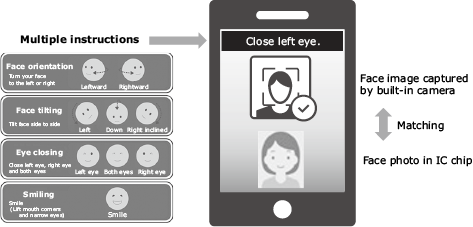
2.3.3 Face matching
The face photo read in paragraph 2.3.2 is matched with the image of the person’s face captured by the smartphone’s built-in camera. Impersonation using a photo or video is prevented by giving instructions to make some facial movements (winking, face tilting, etc.) and checking the result (Fig. 4). After the face matching, the procedure for account opening or other operation can be started using the calling app together with other application information (place of work, phone number, e-mail address, etc.).
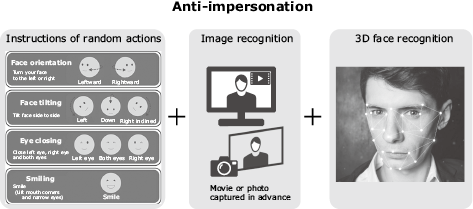
2.4 Enhanced impersonation countermeasures
Personal identification using the IC chip makes it unnecessary to check the thickness of the personal ID document visually by the office worker, which used to be required in previous card processing, so the personal identification becomes exclusively possible with machine alone. The Digital KYC assists automation by enhancing the countermeasures against impersonation that used to be prevented by giving instructions of random actions. Specifically, in addition to the previous method of giving random face action instructions, checking functions are enhanced by combining the function for judging if the image captured by the smartphone’s built-in camera is not the one captured of a still photo or video and the function for judging if the face is a 3D object by checking actions in front of the built-in camera. Therefore the countermeasures against illegal applications based on impersonation are enhanced (Fig. 5).
2.5 Personal identification efficiency improvement
Sharing the personal identification history among eKYC service providers can eliminate the need of personal identification within a certain interval. The personal identification history can be shared among several eKYC service providers by using distributed ledger technology such as blockchain; from the viewpoints of data modification resistance, accountability and non-repudiation, demonstration experiments are being made to improve personal identification efficiency at the time of account opening at banks and securities firms. It is also expected that industry linkages and function expansion for making them possible are advanced and aiming at improving the efficiency of eKYC in the future.
3. Expansion of personal identification service
Because the personal identification service can reduce the time taken for identification and reduce the labor of the users, the scope of its use is expected to expand outside financing services.
- (1)Online non-face-to-face services
Improved safety of e-commerce including mail orders and network auctions and sharing services including housekeeping service and car sharing. - (2)ID check at stores, etc.
Improvement of the ease of personal identification procedures made obligatory by laws and regulations for certain business forms, such as subscription of cellphone and commodities purchase at secondhand stores. - (3)Service combining online and face-to-face methods
Advancement of electronification of personal identification for ticket sales and entrance of concerts and sport events, improvement of ease of reservations of airline tickets and hotels, and improvement of safety at check-ins.
4. Future Perspectives
In the under/post COVID-19 world, it is expected that the use of digital technology will advance rapidly to achieve new consciousness and behaviors of people that are different from before. In the transition to noncontact or online services, personal identification services using the kind of face recognition introduced in this paper will play important roles.
This technology will not be used only for personal identification at the entrance to a service. It may also be used in management of personal data or in information banks in the future.
Since the operations related to personal identification are common to many business types, businesses that provide the service in the form of outsourcing are also expected to come. Speedy provision of services matching the new age will be an important point for competitiveness, and the use of such outsourcing services is also expected to grow.
NEC is determined to continue its contribution to the creation of new digital businesses based on its personal identification and biometric technologies.
- *iPhone and iPad are trademarks of Apple Inc. The iPhone trademark is used under license from AIPHONE CO., LTD.
- *iOS is a trademark or registered trademark of Cisco Systems, Inc. in the U.S. and other countries and is used under license.
- *Android is a trademark of Google LLC.
- *All other company and product names that appear in this paper are trademarks or registered trademarks of their respective companies.
Authors’ Profiles
Senior Manager
Digital Integration Division
Senior Expert
Financial Systems Division
Expert
Financial Systems Division
Project Manager
Digital Business Infrastructure Division
Assistant Manager
Digital Integration Division
Senior Expert
Digital Integration Division

