Global Site
Breadcrumb navigation
Causes of Misdirected E-mail and Countermeasures
NEC Security BlogJun 30, 2023
This article covers Misdirected E-mail which is one of the most typical examples of security incidents. E-mail has become widely used as a necessary item in business scenes, but there are still many Misdirected E-mail. I describe how it occurs and some countermeasures against it below.
Trend of Misdirected E-mail
E-mail is an essential tool in business scenes and used for various purposes and situations such as greetings, reports, announcements, consultation, marketing, negotiation, contract, and so on. Whereas it is useful, it causes Misdirected E-mail once it goes with wrong recipient’s e-mail address or attachment.
Currently Japan is in the following situation. According to the report on incidents related to handling of personal information [2] issued for FY2021 by JIPDEC (Japan Information Processing and Development Center)
[2] issued for FY2021 by JIPDEC (Japan Information Processing and Development Center)  [1], 37.0% of the cause of personal information leakage was Misdirected E-mail. Misdirected E-mail is the most common cause of incidents, and the number has increased by 1.5 times compared to FY2020, so this situation should be taken seriously.
[1], 37.0% of the cause of personal information leakage was Misdirected E-mail. Misdirected E-mail is the most common cause of incidents, and the number has increased by 1.5 times compared to FY2020, so this situation should be taken seriously.
In April 2022, the law of protection of personal information [3] was revised in Japan. Therefore, we have to operate strictly for personal information, for example, it became mandatory to report to the Personal Information Protection Commission and notify the person when personal information leakage occurs.
[3] was revised in Japan. Therefore, we have to operate strictly for personal information, for example, it became mandatory to report to the Personal Information Protection Commission and notify the person when personal information leakage occurs.
Misdirected E-mail causes various troubles even after an incident occurs such as damage to the company’s brand and the business opportunity loss. So, the economic burden on the company is huge.
How Misdirected E-mail Occurs
Except for software flaw, Misdirected E-mail is mainly made by operation mistake (human errors). The following are some examples of specific operation mistakes which lead to Misdirected E-mail.
(1)Typographical Error
Some misdirected e-mails can be sent when the recipient’s e-mail address is manually typed and includes wrong letters or numbers. For example, “yamada@example.com” can be wrongly typed as “yadama@example.com.”
(2)Incorrect Input by Autocomplete Function
Autocomplete function is a helpful function that predicts what word comes next from the input information and suggests the candidate words. However, it presents multiple candidate e-mail addresses, so wrong e-mail address can be picked. For example, when you send an email to a person who has a common name such as John, it is easy to make a selection error because there are multiple candidates for names starting with John.
(3)Confusion of Similar Name or e-mail Address
In case people having same names or similar e-mail addresses belong to same company or organization, an e-mail could be accidentally sent to someone who is not supposed to receive. For example, there may be similar names such as “John Smith” and “Jon Smith” or similar e-mail addresses such as “jon.smith@example.com” and “joe.smith@example.com.”
(4)Misuse of CC (Carbon Copy) and BCC (Blind Carbon Copy)
Besides “To (destination)”, there are CC and BCC. When using CC or BCC function, e-mails are sent to selected addresses, but the disclosure settings are different between CC and BCC. While the e-mail addresses set as CC are open to other recipients, e-mail addresses in BCC will not be shown. Therefore, in case there is a notification e-mail to all customers, the e-mail should be sent as BCC to keep the e-mail addresses private, but all the e-mail addresses could be visible to all recipients if the e-mail addresses are accidentally entered in the CC field.
(5)Inappropriate Setting of Mailing List
Mailing list, a list of multiple e-mail addresses, is commonly used in company or organization and enables to send multiple people at one e-mail address. However, Misdirected E-mail may occur, if the mailing list may not be properly set up and include someone who is not supposed to be in such as resigned employees or third parties. Here is an example of Misdirected E-mail in business situations. If an e-mail is sent while business partner’s e-mail address is accidentally included in the mailing list, some confidential information such as plans for next product may be revealed to the business partner.
(6)Incorrect File Attachments
E-mails can be sent with attachments. Misdirected E-mail also occurs when incorrect file is attached or the attachment includes irrelevant information for the recipients. For example, when sharing some documents with Company A, files for Company B is accidentally attached to an e-mail and sent to Company A. In another example, in case there are two types of files for one matter with different contents, one contains confidential information and the other does not. then the file with confidential information is accidentally attached and sent, information that should not be known will be transmitted.
In addition to the examples above, operation mistakes may also happen when it is done with impatience or fatigue, or even when the computer is slow. As has been listed so far, there are many cases of operation mistakes that cause Misdirected E-mail.
Measures against Misdirected E-mail
As mentioned above, Misdirected E-mail is caused by operation mistakes, but how will the operation mistakes be detected? This chapter is about the multitiered countermeasures against Misdirected E-mail from two perspectives, HOW and WHEN to detect the operation mistakes.
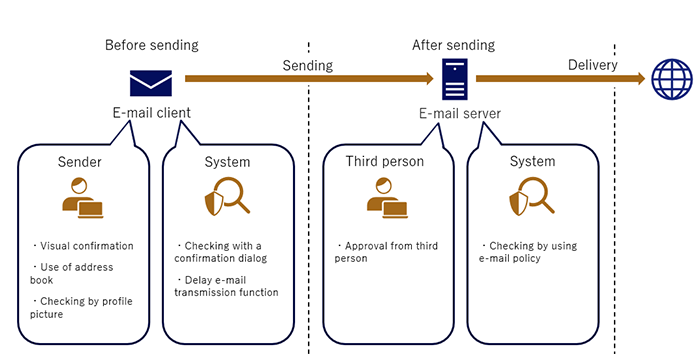
[How to Detect]
- Operation mistakes will be detected by sender, third person (e.g. supervisor), and system.
[When to Detect]
- Operation mistakes will be detected before and after sending.
Checking by Sender Before Sending
Misdirected E-mail can be avoided by checking the e-mail settings by sender before sent. Some examples of countermeasures are below.
Check E-mail Addresses by Eye
First, check the Email addresses by eye before you send E-mail. The risk of the Misdirected E-mail should be minimized by sender him/herself by checking the e-mail before sending. By making it a habit, the sender can notice something in the e-mail is wrong in advance, for example, situation that the e-mail has more CCs than usual.
Using Address Book
When you type the e-mail addresses manually, similar but wrong e-mail address may be selected from past typing history or the autocomplete function. In order to prevent this, e-mail address book that links company, name, and address helps well. Address book enables to confirm the e-mail address by not only finding the e-mail address from the name, but also searching for the name from the e-mail address.
Checking by Profile Picture
In some e-mail software, you can add the pictures to address book . It will be easier to identify the correct e-mail address and reduce the mistake of selecting the recipient by registering the face photo or company’s logo in the address book. Also, some e-mail software linked with authentication infrastructure can automatically acquire and display the face photo from the authentication infrastructure. There is no reason not to take advantage of it.
Checking by System Before Sending
An automatic e-mail check application will comprehensively check the e-mails for problems before sending. Some example of countermeasures are below.
Checking with a Confirmation Dialog
There is a feature for the system to automatically check an e-mail before sending and display a dialog which prompts the sender for final confirmation with reviewing the check result. Most e-mail clients display the list of recipient e-mail address and prompt to check if all the e-mail addresses are correct. Some e-mail clients prompt us to confirm some important points by senders, for example, whether the recipient is a business partner or related company, and the file is properly attached. Organizing this information and displaying the confirmation dialog allows senders to make sure the e-mail is ready to be sent.
Delayed E-mail Transmission Function
It often happens to notice mistakes in attachments and recipient e-mail addresses just after sending. Many e-mail clients have a function that delays the time between pressing the send button and the actual send. As a rough guide, it seems good to delay about 1-5 minutes. It will no longer be real-time e-mail correspondence, but it will prevent Misdirected E-mail at the last minute.
Checking by Third Person After Sending
E-mail is not directly sent from the sender’s environment, but via the e-mail server. For example, when an e-mail is sent from a company, it is delivered via the company’s e-mail server. In this case, the e-mail can be put on hold at the company’s e-mail server for a certain time to see if there is nothing wrong. In below, here is a countermeasure checked by someone other than sender after sending.
Approval from Third Person
For example, when a subordinate sends an e-mail to an outside company, the supervisor can receive the information and give an approval for the external sending. In this way, the supervisor can double-check the recipients’ e-mail addresses, e-mail text, and the attachment. However, this is not efficient since it is too much work for the supervisor to check all external e-mails. It is better to limit the use of third-person approvals, such as only when the e-mail will be sent to an important sales partner.
Checking by System After Sending
By coordinating an e-mail checking system and the e-mail server of the company, e-mails in transit can be automatically and exhaustively verified to make sure everything is in order. Since this is done by system, a massive amount of e-mail will be processed in real-time. Some examples of countermeasures by system after sending are below.
Checking by E-mail Policy
There is a way to prevent Misdirected E-mail by creating an e-mail policy and automatically checking all e-mails sent from the company. For example, in the case of an incident in which the e-mail addresses of all customers were put into CC instead of BCC, it will be prevented by creating a policy which sets the maximum number of e-mail addresses that can be included in CC. However, even if the policy is violated, it does not mean that all e-mails have problems because sometimes the policy is not up-to-date or not set up for new customers. If an error is detected by the policy, it is better to return the e-mail to the sender and have it confirmed.
To Prevent Misdirected E-mail
Ideally, instead of using only one countermeasure, Misdirected E-mail should be prevented in multiple layers by combining multiple measures. Operation mistakes can be occurred by not only the sender but also the third person who checks e-mails and the system setter. Therefore, it is necessary to implement the countermeasures in a multi-layered way and to minimize the risk of Misdirected E-mail.
Incidentally, other than the countermeasures above, cloud storage is another option.
In recent years, it has become more familiar to share files with people outside the company as cloud storage has become common. Thereby, instead of attaching files directly to e-mails, uploading files to cloud storage with managing who can access them is another countermeasure. Even if Misdirected E-mail occurs, it can limit the damage because the third-party will not obtain the files by setting the access rights appropriately. However, there are another risk to consider. For example, if the access privileges or disclosure range is set incorrectly, files in the cloud storage can be published to the world. In addition to this risk, if a third party obtains the URL indicating the file location in the e-mail text and accesses it, the information can be stolen.
Conclusion
Although e-mail has come to wide use and become an essential item of business scenes, the perfect method to prevent Misdirected E-mail is not established yet. Therefore, first of all, every single user must use e-mail with special caution. For the cases where this is not enough, third person confirmation or a system for reducing mistakes should be introduced and multi-layered measures should be considered.
Operation mistakes happen to anyone at any time. No matter how busy the situation is, it is important to pause a moment to confirm the e-mail addresses or attachments are correct. By checking calmly, the hints of small differences from usual and mistakes may be noticed. I hope this article helps to prevent Misdirected E-mail for each individual and company.
References:
- [1]一般財団法人日本情報経済社会推進協会(JIPDEC)
 https://www.jipdec.or.jp/
https://www.jipdec.or.jp/ - [2]JIPDEC, 2021年度「個人情報の取扱いにおける事故報告集計結果」
 https://privacymark.jp/news/2022/other/1007.html
https://privacymark.jp/news/2022/other/1007.html - [3]個人情報保護委員会, 令和3年 改正個人情報保護法について
 https://www.ppc.go.jp/personalinfo/minaoshi/
https://www.ppc.go.jp/personalinfo/minaoshi/
Profile
Hidefumi Yamada
Security Engineering Center, Secure Technology Development Group
With experience in network design and mainframe development, Hidefumi Yamada is currently dedicated to the development of security-related services for the NEC Group.
