Global Site
Breadcrumb navigation
Software Updates for PCs, Smartphones, and Tablet Devices
NEC Security BlogJun 10, 2022
The topic of today’s security blog is software updates for PCs, smartphones, and tablet devices.
The information in this article is current as of June 2022.
Introduction
Nowadays, there are many personal devices such as PCs, smartphones, and tablets that everyone uses. These information devices have a software update function that adds new features, fixes bugs, and provides security updates when vulnerabilities are found.
However, there are various issues such as unclear end of support date for how long these software updates will be available, and delays in providing security updates after a vulnerability is reported. In this article, I would like to take a look at the story behind such issues surrounding software updates. Please note that the topic here mainly targets personal devices such as PCs, smartphones, and tablet devices, and it does not cover servers and IoT devices.
Example of Vulnerabilities that Affect Multiple Products, but the Timing of Fixes Differs for Each Product
On May 26, 2022, security updates were released for several Apple products. Among them, there were two notable vulnerabilities: the Apple AVD (Kernel extension for audio and video decoding) vulnerability tracked as CVE-2022-22675 and the Intel Graphics Driver vulnerability tracked as CVE-2022-22674. The details of these two vulnerabilities are omitted here, but both are serious vulnerabilities that have been reported to be exploited. The CVE-2022-22675 exists in macOS Big Sur, which is the version preceding the latest macOS Monterey (an OS for MacBook and iMac), tvOS (an OS for AppleTV), and watchOS (an OS for Apple Watch). The CVE-2022-22674 exists on macOS Big Sur and macOS Catalina, which is two versions preceding the latest macOS Monterey. Both vulnerabilities were fixed in a security update released on May 27.
However, these two vulnerabilities had been fixed on March 31, 2022, about two months earlier, targeting macOS Monterey (an OS for MacBook and iMac), iOS (an OS for iPhone), and iPadOS (an OS for iPad).
As it might be a bit complicated, it would be easier to comprehend the table below showing the two vulnerabilities, the affected OSes, and the date of security updates released.
| Vulnerability | March 31, 2022 | May 27, 2022 |
| CVE-2022-22674 | Fixed for macOS Monterey | Fixed for macOS Big Sur and macOS Catalina |
| CVE-2022-22675 | Fixed for macOS Monterey, iOS, and iPadOS | Fixed for macOS Big Sur, tvOS, and matchOS |
Table-1: The two vulnerabilities, the affected OSes, and the date of security updates released
As shown in the table above, as of March 31, 2022, the vulnerabilities had been fixed only for Monterey (the latest version of macOS) and iOS and iPadOS which are widely used. And the vulnerabilities had still existed on the older version of macOS such as Big Sur and Catalina, and tvOS and watchOS which have relatively fewer users remained unaddressed.
When security updates for vulnerabilities are released, attackers may analyze the update program to see what kind of fixes have been made and then target products that have not yet applied the security updates. In this case, multiple products had similar vulnerabilities and since only some of them were initially fixed, other unpatched products would have been targeted by the attacks.
Example of Varying Software Update Periods Depending on Hardware
For personal devices, it is often not specified by the vendor that how long software updates will be available. Therefore, it is possible that one may only realize that the device being used is no longer supported until the update is actually released.
Again, here is an example of Apple products. The table below shows the release dates of hardware and the latest iOS versions that can be installed on that hardware (as of the time of writing this blog post) for iPhones released in Japan (from the 3GS onwards).
| Hardware | Release Date | The latest iOS | Final update date of iOS |
| iPhone 6s onwards | September 25, 2015~ | 15.5~ | May 16, 2022~ |
| iPhone 6 | September 19, 2014 | 12.5.5 | September 23, 2021 |
| iPhone 5s | September 20, 2013 | 12.5.5 | September 23, 2021 |
| iPhone 5c | September 20, 2013 | 10.3.3 | July 19, 2017 |
| iPhone 5 | September 21, 2012 | 10.3.4 | July 23, 2019 |
| iPhone 4s | October 14, 2011 | 9.3.6 | July 23, 2019 |
| iPhone 4 | June 24, 2010 | 7.1.2 | June 30, 2014 |
| iPhone 3GS | June 19, 2009 | 6.1.6 | February 21, 2014 |
| iPhone 3G | July 11, 2008 | 4.2.1 | November 22, 2010 |
Table-2: iPhone release dates and the final iOS update dates
Based on this table above, the latest iOS versions, iOS 15, can be installed on iPhone 6s or later. At least for iPhone 6s or later (iPhone models released after September 25, 2015), it is likely that the latest software updates can be received. However, regarding iPhone models prior to iPhone 6 that cannot be updated to iOS 15, updates are not actively provided as it can be seen from the last update date of iOS.
Also, you may wonder that the iPhone 5 released a year earlier than the newer iPhone 5c, has a newer version of iOS. This is due to a GPS hardware issue in the iPhone 5, which was fixed with a software update. Therefore, since the iPhone 5c was not affected by this hardware issue, there was no need to apply the newer iOS version, resulting in a reversal of the last update date. It seems that Apple responded promptly to this critical issue because it would render internet connection impossible if not fixed. However, it is speculated that regular fixes for vulnerabilities are no longer implemented.
Here is another similar example, Chromebooks. Chromebooks are the laptop PCs that are equipped with Chrome OS provided by Google. Unlike Apple, which provides hardware and OS as one, various hardware manufacturers have produced products with Chrome OS.
Chromebooks have an automatic update function for Chrome OS without the user being aware of it, but unfortunately it is not possible to update forever in the future. Updates can only be made within the period specified as the “Auto Update Expiration date” and will not be performed after that. “Auto Update Expiration date” for each model is available on Google’s website. As an example, the expiration date for NEC Chromebook is as follows.
| Product | Auto Update Expiration date |
| Chromebook Y1 | June, 2027 |
| Chromebook Y1 Gen2 | June, 2027 |
| Chromebook Y1 Gen2A | June, 2026 |
| Chromebook T1 Gen3A | June, 2029 |
| Chromebook Y2 | June, 2027 |
| Chromebook Y3 | June, 2029 |
Table-3: Auto Update Expiration date for NEC Chromebook
Example of Hardware Constraints that Prevent Upgrades
Lastly, let’s take a look at an example of a Windows PC. The Following are the currently supported versions for the Windows OS for personal computers (as of the time of writing this blog post).
| Version | End of Support Date |
| Windows 8.1 | January 10, 2023 |
| Windows 10 | October 14, 2025 |
| Windows 11 | Undetermined |
Table-4: The End of Support Date for Windows
During the support period, Windows will automatically receive security updates on a regular basis. However, after the support period, security updates will no longer be delivered, resulting in an increase in unfixed vulnerabilities if the system continues to be used. Therefore, in order to continue receiving updates, it is necessary to upgrade to a supported version before support ends. Upgrade from Windows 8.1 to Windows 10 and from Windows 10 to Windows 11 are free, but there may be cases where the upgrade cannot be performed if the hardware does not meet the requirements.
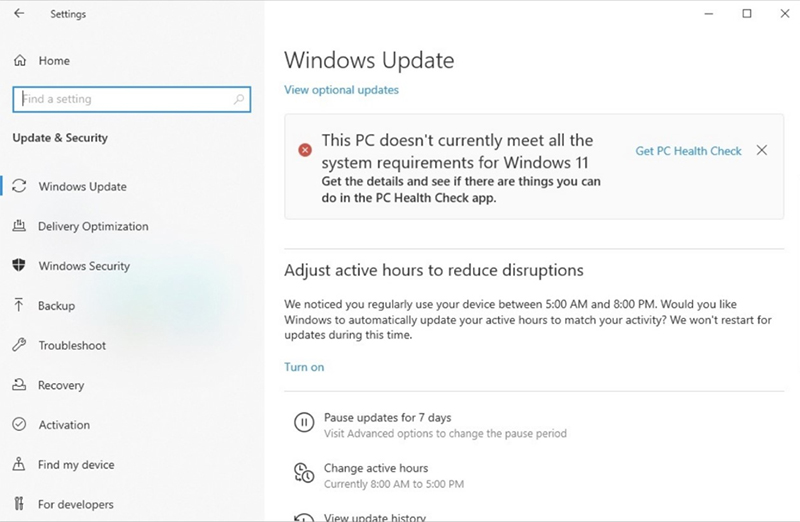
Also, going back to the example of iPhone above, the latest iOS cannot be used on older hardware, but software updates for the older hardware may still be provided if there is a issue. However, since the support period is not specified, it is unclear how long such software updates will be provided.
Considerations for Continuously Receiving Software Updates on Personal Devices
So far, we have seen several examples of software updates on personal devices such as PCs, smartphones, and tablets. Finally, let’s summarize the points to note in order to keep receiving software updates.
First of all, when multiple OS versions are available for the same hardware, it is advisable to use the latest version whenever possible. The reason for this is that, as mentioned in the first example, even among the same macOS, the latest version is often quicker to receive vulnerability fixes, while fixes for older versions may be postponed. Ideally, it is better to use the latest versions, such as macOS Monterey for macOS and Windows 11 for Windows. However, if an upgrade is not available to such latest versions due to hardware constraints, it is recommended to use the newest version as much as possible.
Next, hardware that is no longer eligible to receive software updates after the support period expires should be replaced, even if it is not broken. This is because any newly discovered vulnerabilities will not be fixed and it will make it difficult to maintain a safe usage. Also, even in cases where the support period is not specified, it is better to consider replacing the device once it can no longer be upgraded to the latest version. Specifically, in the case of iPhone, this applies to iPhone 6 or earlier, which cannot be upgraded to iOS 15 series.
And of course, it is important not to neglect software updates even for hardware within the support period. In many cases, you can set up automatic software updates, so it is highly recommended to enable automatic updates settings if possible.
Conclusion
In this article, we took a look at the importance of software updates for personal devices such as PCs, smartphones, and tablets. As shown in this article, some devices have clear support deadlines, while others are unclear how long they will be supported. It may be worth checking whether your own devices are still supported and they are being regularly updated to the latest version.
References
- [1]
- [2]
- [3]
- [4]
- [5]
- [6]
Profile

Satoshi Gunji, CISSP
Security Engineering Center, Cyber Security Intelligence Group
Satoshi Gunji primarily engages in the tasks of collecting and analyzing threat information, and delivering it to the people who need it. My main qualifications include CISSP and Information Security Specialist.
 https://support.apple.com/en-us/HT201222
https://support.apple.com/en-us/HT201222