Global Site
Breadcrumb navigation
Look-alike URL ~Beware of Misleading URL~
NEC Security BlogJan 7, 2022
Have you ever heard of homograph attack or attacks which use it to mislead URL? In this blog, the URL which intentionally misleads users to wrong URL is called “misleading URL” for explanatory convenience because there is no official name. This term mainly refers to a spoofed URL using a similar string of characters that are difficult to distinguish from legitimate one, and that attackers use to coax the target into clicking on malicious URL.
In recent years, as seen in the increase in phishing attacks, the threat has increased, this blog explains misleading URL which is one of the techniques of those attacks and homograph attack which is one of the methods to achieve misleading URL with examples.
1.Examples of Misleading URL and Homograph Attack
There is an article of the collaborative project by Google and The University of Illinois at Urbana-Champaign published in 2020  [1]. In this article, there is an experimental description in terms of how many misrecognitions of misleading URL occur. In the results, it is stated that only approximately 7% of participants fell for phishing URLs that did not use deliberately misleading strings, but 60% of participants fell for misleading URL.
[1]. In this article, there is an experimental description in terms of how many misrecognitions of misleading URL occur. In the results, it is stated that only approximately 7% of participants fell for phishing URLs that did not use deliberately misleading strings, but 60% of participants fell for misleading URL.
“Misleading” here refers to things that visually elicit misunderstanding by replacing the characters in legitimate URLs with other characters resemble them as described above. And one of the typical methods is called “Homograph Attack.”
Here are some examples of misleading URL from the article mentioned above.
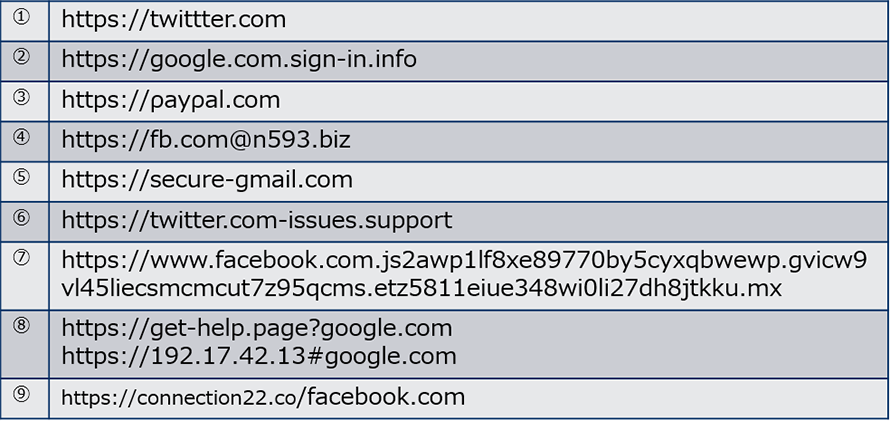
 [1]
[1]- ※Please do not access the listed URLs.
Do you realize where the misleading parts are?
The relevant parts are highlighted in blue in figure-2.
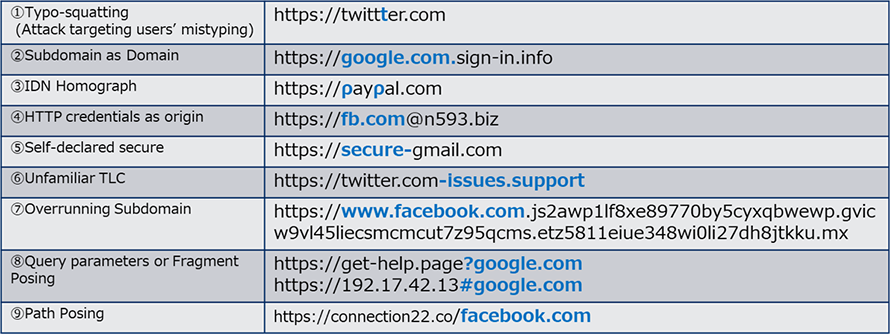
As seen from Figure-2, it is probably more difficult than you might think to tell where the confusing part is in the misleading URLs. In recent years, even these spoofed URLs using HTTPS protocol as SSL certificates are much easier to obtain for free, so it is getting harder than ever to distinguish the difference.
The following is some examples of homograph attacks which are typical methods of misleading URL.
Like the example ③ of Figure-2, homograph attack has been used for a long time as a classic attack method that misleads people by using confusing characters. However, with the recent spread of IDN (Internationalized Domain Name), and now non-ASCII characters such as Unicode are also available to use for URLs as well as the strings used so far(※). This has allowed us to design URLs in more ways, which has led to an increase in patterns that are very difficult to distinguish.
- ※Previously, only alphabet (A to Z), numbers (0 to 9), hyphen (-), and dot (.) in ASCII code were available.
Can you distinguish where the misleading part is in the examples of Figure-3? (They are shown in “Meiryo”(Japanese Font))

Figure-4 below shows the answer. It may be look-alike because of the font, but actually it can be also created with more confusing fonts. Considering the possibility that URL string with those confusing font may be included in a web page or an HTML e-mail, homograph attack is still a threat even though it has been around for a long time.
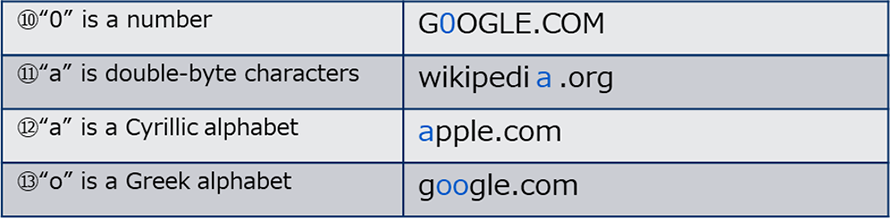
2.Countermeasures against Misleading URL and Homograph Attack
What should we do about these attacks which are ancient methods but still a threat today? The followings are three possible countermeasures.
I.Use the Latest Common Browser
For example, Google Chrome has an warning function that displays a warning on URLs which resemble well-known websites  [2] and Microsoft Edge officially implements a web filter function
[2] and Microsoft Edge officially implements a web filter function [3]. Needless to say, these measures alone are still not perfect enough, but using the latest version of the browser instead of the old one could reduce risk.
[3]. Needless to say, these measures alone are still not perfect enough, but using the latest version of the browser instead of the old one could reduce risk.
II.Verify the Safety of the Website / Access Authorized Websites
For one example, it is possible to see if the website is safe or legitimate by using a service  [4] that verifies the safety of the website by entering the URL. However, this may not be practical because it is hard to check the safety of a website every single time when visiting it. Apart from that, there are several other ways to do it, such as bookmarking frequently used websites (legitimate websites) or visiting those websites via search engines.
[4] that verifies the safety of the website by entering the URL. However, this may not be practical because it is hard to check the safety of a website every single time when visiting it. Apart from that, there are several other ways to do it, such as bookmarking frequently used websites (legitimate websites) or visiting those websites via search engines.
III.Implement a Solution
Some security solutions use functions such as web filters to check if the target site/URL is safe and allow access if there are no problems[5]. Although it costs, this is a highly feasible method considering safety and convenience.
IV.(Extra Option) Trust JP domain
As a matter of fact, the characters that can be used in JP domain names are limited to Japanese “kanji”, “kana”, and English alphanumeric characters, so the domain names that contains characters that are likely to be used in homograph attack, such as the Greek alphabet mentioned in the examples, cannot be registered. (  https://日本語.jp/access/phishing.html)
https://日本語.jp/access/phishing.html)
However, even kanji, there are many characters that look similar, so it is difficult to eliminate homograph attacks completely. It is necessary to pay attention not only to misleading URL and homograph attack but also other attacks such as phishing that use more sophisticated methods like URI spoofing or concealment of the destination.
3.Conclusion
What is in your thoughts about the theme of this blog, misleading URL and homograph attack used on phishing sites? These attacks do not require sophisticated methods, but anyone can fall victim to them. Please be noted that there is a risk of falling into such traps when accessing URLs listed in e-mails or websites.
References:
- [1]Reynolds, Joshua & Kumar, Deepak & Ma, Zane & Subramanian, Rohan & Wu, Meishan & Shelton, Martin & Mason, Joshua & Stark, Emily & Bailey, Michael. (2020). Measuring Identity Confusion with Uniform Resource Locators. 1-12. 10.1145/3313831.3376298. (
 https://storage.googleapis.com/pub-tools-public-publication-data/pdf/6c4c8018ca2875aaf3fc19819154ed0185af2796.pdf)
https://storage.googleapis.com/pub-tools-public-publication-data/pdf/6c4c8018ca2875aaf3fc19819154ed0185af2796.pdf) - [2]THE URLEPHANT IN THE ROOM,Google,
 https://www.usenix.org/conference/enigma2019/presentation/stark
https://www.usenix.org/conference/enigma2019/presentation/stark - [3]Microsoft Edge で Web サイトや検索結果をフィルター処理する
 https://support.microsoft.com/ja-jp/account-billing/microsoft-edge-%E3%81%A7-web-%E3%82%B5%E3%82%A4%E3%83%88%E3%82%84%E6%A4%9C%E7%B4%A2%E7%B5%90%E6%9E%9C%E3%82%92%E3%83%95%E3%82%A3%E3%83%AB%E3%82%BF%E3%83%BC%E5%87%A6%E7%90%86%E3%81%99%E3%82%8B-3034d91e-5efa-9fbe-1384-46009f087ccf
https://support.microsoft.com/ja-jp/account-billing/microsoft-edge-%E3%81%A7-web-%E3%82%B5%E3%82%A4%E3%83%88%E3%82%84%E6%A4%9C%E7%B4%A2%E7%B5%90%E6%9E%9C%E3%82%92%E3%83%95%E3%82%A3%E3%83%AB%E3%82%BF%E3%83%BC%E5%87%A6%E7%90%86%E3%81%99%E3%82%8B-3034d91e-5efa-9fbe-1384-46009f087ccf https://support.microsoft.com/en-us/account-billing/filter-websites-and-searches-using-microsoft-family-safety-3034d91e-5efa-9fbe-1384-46009f087ccf
https://support.microsoft.com/en-us/account-billing/filter-websites-and-searches-using-microsoft-family-safety-3034d91e-5efa-9fbe-1384-46009f087ccf - [4]Virus Total,
 https://www.virustotal.com/gui/home/url
https://www.virustotal.com/gui/home/url - [5]InterSafe WebFilter製品機能, NEC,
https://jpn.nec.com/intersafe/introduction.html
Profile

Asuka Suzuki
Security Engineering Center,Vulnerability Management Group and Talent Management Group
Asuka Suzuki Engaged in the management and promotion of vulnerabilities in the NEC Group. In addition to her primary responsibilities, she also contributes to security education and talent development.