Global Site
Breadcrumb navigation
The Reasons Why Dual NIC is Risky: Consideration from NIST SP800-82
NEC Security BlogJun 18, 2021
Introduction
Designing the network configuration of a system is one of the most common tasks for system engineers.
In the process of considering the network configuration, there is a task called network segmentation, and different network addresses are assigned depending on the role and installation location of the device. In network segmentation, there is a method of using devices such as firewalls and routers, but there is also a method called “Dual Network Interface Cards/Dual-homed Computer,” in which two NICs (network interface cards) are inserted into a server or PC to divide the network. However, it is generally considered that the latter is not recommended due to security reasons.
This blog is discussing why network segmentation by dual NIC is risky by reference to NIST SP800-82 as a guide for building secure Industrial Control System (ICS).
Network Segmentation in NIST SP800-82
NIST SP800-82  [1] is a guide on how to establish secure ICS. “5 ICS Security Architecture” of this guide introduces how to divide the corporate network and the control network. Since the property of network traffic is different between the corporate network and the control network, the network should be divided into two parts so that even if a network failure occurs on one side, the other side can stay safe. Also, the connection between these two networks should be kept to a minimum. This is because the control network deals with physically acting control devices such as sensors and actuators, so if a security incident such as a malware infection occurs on the corporate network and spreads to the control network, the damage will extend to the real space through the control device.
[1] is a guide on how to establish secure ICS. “5 ICS Security Architecture” of this guide introduces how to divide the corporate network and the control network. Since the property of network traffic is different between the corporate network and the control network, the network should be divided into two parts so that even if a network failure occurs on one side, the other side can stay safe. Also, the connection between these two networks should be kept to a minimum. This is because the control network deals with physically acting control devices such as sensors and actuators, so if a security incident such as a malware infection occurs on the corporate network and spreads to the control network, the damage will extend to the real space through the control device.
In order to minimize the network connection between the corporate network and the control network, it has to be considered how to connect and divide the network, for example, passing only the necessary communication between the two networks. Although NIST SP800-82 is a guide on ICS security, the idea of network segmentation is also important in general information systems which have increased the impact on real space, such as IoT (Internet of Things).
NIST SP800-82 introduces the following methods for dividing the corporate network and the control network.
The bigger the number, the higher the security level, but also the higher the cost.
-
Dual-Homed Computer/Dual Network Interface Cards
-
Firewall
-
Firewall and Router
-
Firewall with DMZ
-
Paired Firewalls with DMZ
1. dual-homed computer/dual network interface cards in above is dual NIC that divides a network by inserting two NICs into a server or PC. If the server or PC does not have appropriate security measures in place, network traffic could pass through another network, so this method should not be used for network segmentation.
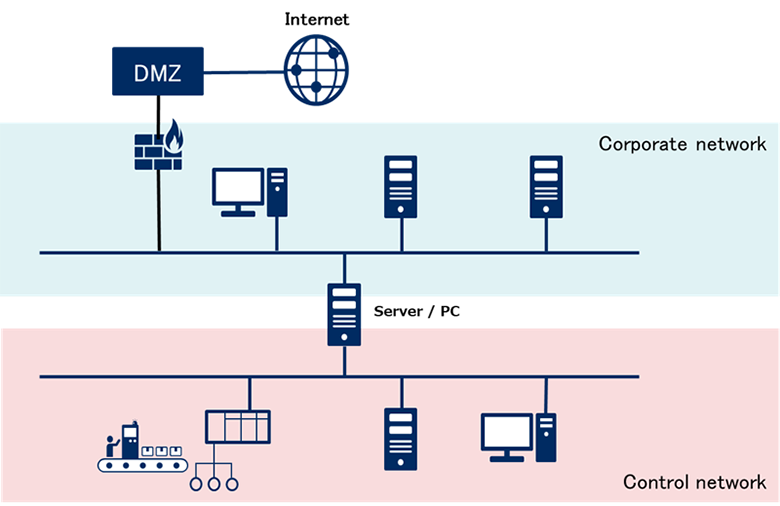
As shown in above, the passage of network traffic is listed as a threat in NIST SP800-82, but other possible threats can be also considered.
Threats from Dual NIC
In the following, the two divided networks are respectively the corporate network and the control network in accordance with the NIST SP800-82 example.
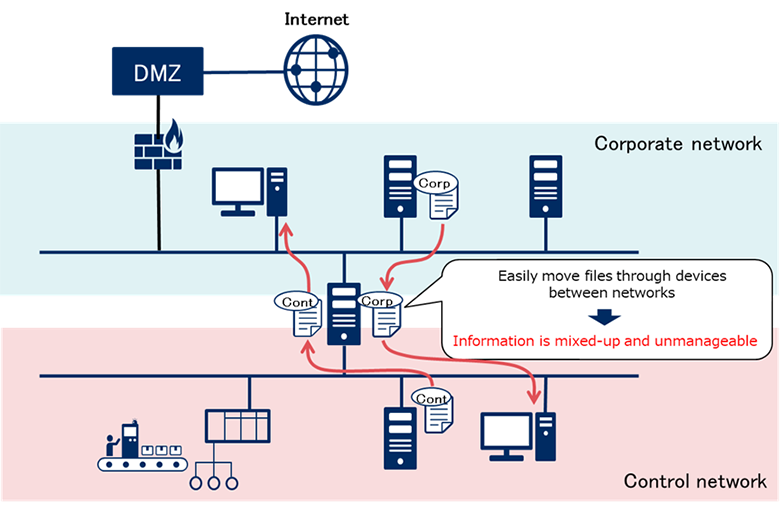
① Information Mixing by File Sharing
Servers and PCs have file storing function, and can share files with other servers and PCs through the network. When network is divided by dual NIC, files can be directly shared on both the corporate and control network. Therefore, it is easy to move files stored on the servers or PCs on the corporate network to the control network, and vice versa, so the files stored on each network may be mixed as a result. From the perspective of information management, it is unfavorable that files that originally located on different networks are mixed together. Even if operational rules are established to restrict file movement, file mixing may occur by employees who are not experienced enough or have a poor understanding of the operational rules.
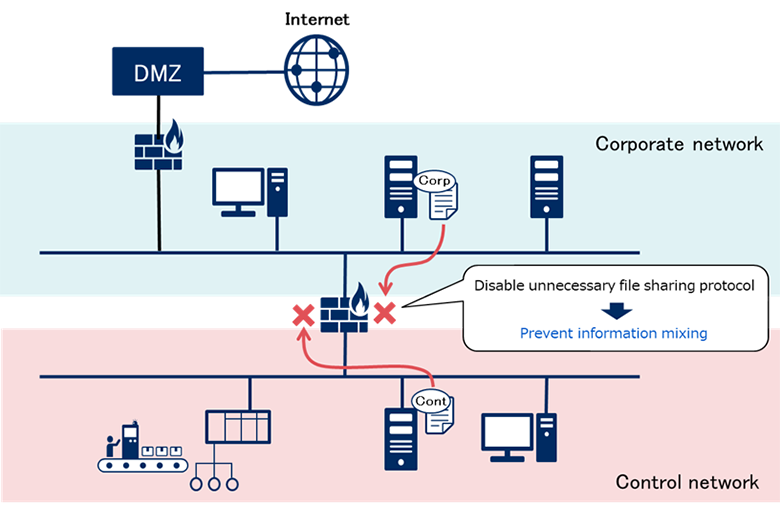
To prevent the file mixing from different networks, network should be divided by network device such as firewall, rather than servers or PCs with dual NIC. In general, network devices are not equipped with file sharing features, so files cannot be moved by directly operating the network devices. Also, by setting up access control by firewall, it allows to disable SMB (Server Message Block) which is a file sharing protocol used in Windows, and restrict the servers and PCs that can share files.
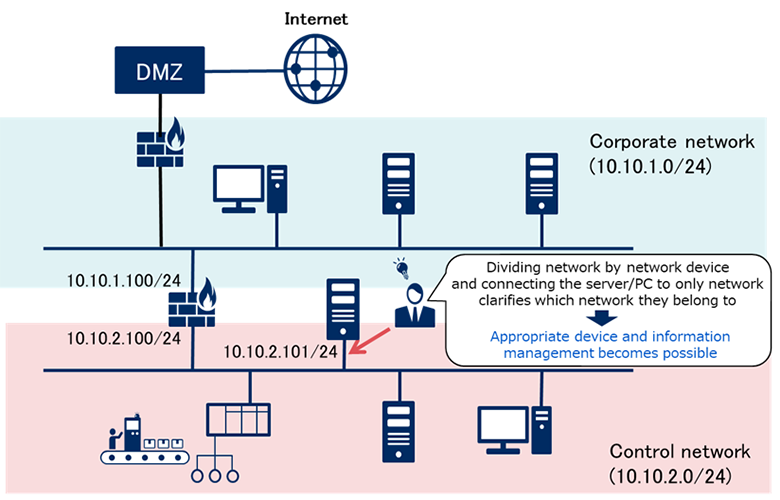
② Unclear Network Belonging of the Server/PC
The network to which the server or PC belongs is usually determined by the IP address assigned to the NIC. Although for server or PC with dual NIC, it is difficult to clearly determine whether it belongs to the corporate network or the control network. Some design documents or specifications define which network the server or PC with dual NIC belongs to. However, since it is not practical to check those documents every time, the network to which the server or PC belongs tends to be unclear. Therefore, it is difficult to grasp which network the files and data belong to and are managed, and there is a possibility that information will be mixed up in the same way as 1. above.

In order to clarify which network a server or PC belongs to, divide the network by network devices such as firewall, and also connect the server or PC to only one network. By connecting the server or PC to only one network, it becomes clear where the network belongs, and appropriate device and information management will be performed. Here, the question may arise as to which network the network device belongs to. It is said that a network device belongs to both the corporate network and the control network because it has two distinct roles: to divide a network and to be a gateway to another network.
③ Exploitation of Vulnerabilities / Used as a Jump Server
Compared to network devices such as firewall, various features and services are running on servers and PCs. Therefore, vulnerabilities tend to be detected in large numbers, and once vulnerabilities are found in features and services installed in the servers and PCs, attackers relentlessly try to penetrate by targeting those vulnerabilities. In case successfully penetrated and servers or PCs used for network segmentation became a jump server, the damage of the attack extends to adjacent networks.
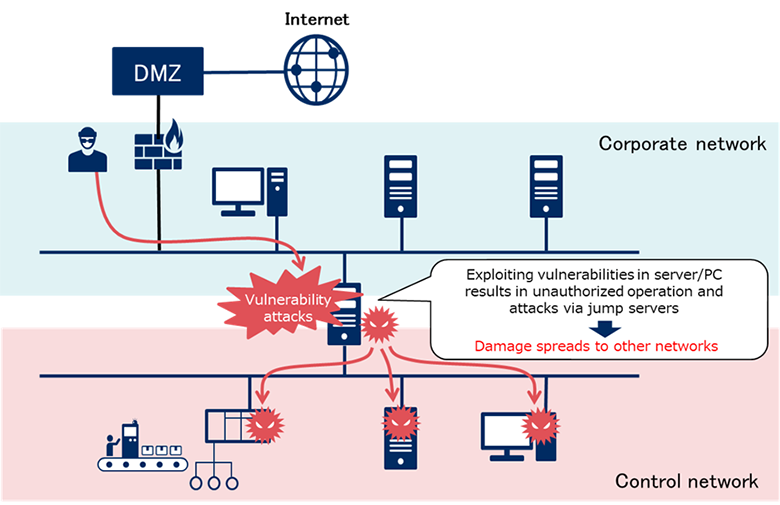
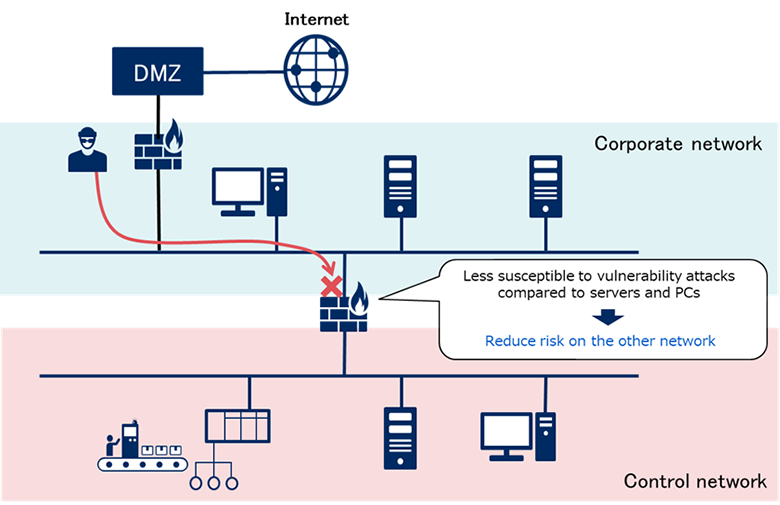
Generally, fewer features and services are running within network devices than servers and PCs. Therefore, there are not many types of attacks aimed at the vulnerabilities. From this point of view, network segmentation is still better to be performed by network devices such as firewall. Having said that, it does not mean vulnerabilities will not be found in network devices, it is always essential to collect information on the vulnerabilities of the network devices used.
Summary
The reasons why dual NIC is considered risky have been examined in this article. As network segmentation with dual NIC may present various potential risks both technical and operational, other methods described in NIST SP800-82 should be chosen for network segmentation rather than dual NIC.
When looking at the network diagrams of systems published on the internet, there would be some cases of network segmentation by a server or PC with dual NIC. People who have knowledge of network may be able to read the fact that even if the network is divided by dual NIC in the configuration diagram, firewalls or routers should be used for actual network segmentation. Then, they will build the system with network devices which is suitable for network segmentation. However, inexperienced people may only look at the information on configuration diagram and build a network by inserting two NICs, which is risky.
NIST SP800-82 describes secure methods of ICS construction, yet the concept of network segmentation is not limited to ICS. The key is to understand the role and purpose of the system well, and thereby make an appropriate network segmentation.
Reference
- [1]NIST SP800-82 Rev.2
 https://csrc.nist.gov/publications/detail/sp/800-82/rev-2/final
https://csrc.nist.gov/publications/detail/sp/800-82/rev-2/final
日英対訳版 (JPCERT/CC) https://www.jpcert.or.jp/ics/information02.html
https://www.jpcert.or.jp/ics/information02.html
Profile

Kotaro Kusakabe, CISSP/RISS(Registered Information Security Specialist)
Security Engineering Center, Security Implementation Technology Team
Kotaro Kusakabe Joined the Security Engineering Center in 2019 and engaged in secure development support for systems and services provided by the NEC Group.
He Completed the 2nd Term Core Human Resource Development Program of the IPA Industrial Cybersecurity Center.