Global Site
Breadcrumb navigation
Technology for Automatic Cyber Attack Risk Assessment
Featured TechnologiesNovember 5, 2018

Today, the threat of cyber attacks is no longer limited to the ICT field, and numerous attacks have also targeted control systems and the IoT field. Cases involving control systems have occurred that threaten critical infrastructures by bringing power systems and factory operations to a halt.
Now, in increasing numbers of cases, control systems that were previously not connected externally are being used for remote monitoring over a network. For this reason, ransomware within control systems has spread, and there have even been reported cases of production lines being forced to shut down. Cyber attacks targeting critical infrastructures have also been on the rise (Note 1). It was reported that the malware known as TRITON was used in 2017 to stop production in an industrial plant in the Middle East. Like Stuxnet, which was used to target Iranian nuclear facilities in 2010, and BlackEnergy, which caused a power outage in the Ukraine in 2015 and 2016, this type of malware targets control systems. Cyber attacks that target control systems are intended to bring about major social and economic impact and upheaval through physical destruction which causes power outages and other adverse events, and over the coming years, these attacks are expected to increase in quantity and in sophistication. For this reason, security measures are required for a wide range of industrial plants and industrial control equipment.
The approaches to security measures differ significantly between information systems and control systems. In information systems, generally, security measures are given priority, and software updates and anti-malware products are installed even if they have a slightly adverse impact on computer processing performance. However, in control systems, utmost importance is placed on availability so that processes can continue to operate without delays. And so, security measures are not properly implemented due to concerns about their impact on the operation of the software and control equipment. Also, the misunderstanding persists that equipment is not vulnerable to malware infection when it is not connected to the Internet or an information systems.
If cyber attacks are directed at control systems for critical infrastructure, and damage due to physical destruction occurs, it could result in long-term stoppage of operations. To ensure that this does not happen, security measures must be properly implemented, but implementing security measures on all component equipment may be unrealistic in terms of cost and time. And so, risk analysis becomes important for control systems and the information systems connected to them. Risk analysis is conducted to find locations susceptible to cyber attack and routes easily accessible to attack for clarifying the potential impact of an attack. However, from the standpoint of availability, it is extremely difficult to conduct a risk analysis using an actual system whenever new vulnerabilities or attack methods are reported.
This led NEC to develop technology that conducts analysis automatically without using the actual system for indicating the degree of risk exposure of equipment not just in the ICT field, but also for IoT and control systems. This analysis provides visualization of vulnerabilities that could be exploited and potential attack routes to enable determination of where security measures should be implemented and their priority.
Features of the New Technology
-
Virtual models that also support control systems, not only ICT systems
For control systems, different information from information systems is required to conduct a risk analysis, such as the air-gap environment that is isolated from the network and the control system-specific devices (PLC: Programmable Logic Controller). In the technology for automatic cyber security risk assessment developed by NEC, detailed information required for risk analysis, such as the information-based systems making up the control system and component information of control system-specific devices, communication data between devices, and data transfer status in the air-gap environment, is automatically collected for building a virtual model.
In this virtual model, the composition of the entire system and the flow of data are visualized, and a risk analysis simulation is used to enable accurate and proper understanding of the locations where security measures are required.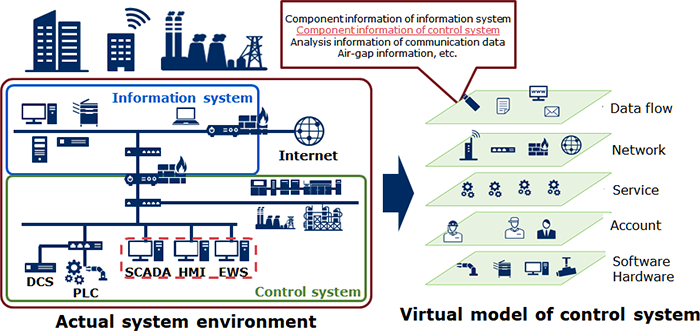
Fig 1: Virtual model -
Analysis database and risk analysis simulations for narrowing down potential attack scenarios
Cyber attacks are conducted by exploiting communication data and vulnerabilities and improper settings in the system. For this reason, in addition to taking security measures for vulnerabilities in the equipment and system, there must also be an understanding of how vulnerabilities and communication data are actually exploited to conduct an attack. Cyber security experts analyze cyber attacks using public information such as CVE (Common Vulnerabilities and Exposures), CAPEC (Common Attack Pattern Enumeration and Classification), and the ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework, which were primarily developed, organized, and implemented by MITRE, a not-for-profit organization, with the support of the U.S. government. The severity of a vulnerability is indicated by its CVSS (Common Vulnerability Scoring System) base score, and typically, the priority for the security measures is determined in order of higher CVSS base scores, but in actuality, cyber attacks also exploit vulnerabilities with low CVSS base scores.
Based on attack pattern information that usually only cyber experts can understand, the attack implementation conditions, impact after a successful attack, and other details are analyzed for building a unique set of rules based on the common characteristics of the attack patterns. This analysis database and virtual model are used in simulations to comprehensively generate continuous attack scenarios from the start of an attack until reaching the attack target. In the virtual model, a selected location can also be specified as the attack start point to set vulnerabilities to specific equipment and to enable risk analysis assuming an inside job or zero-day attack.
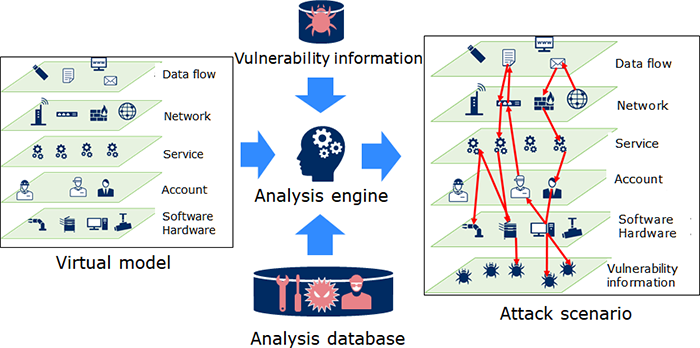
Fig 2: Analysis database -
Simulation of security measures based on analysis results
Attack scenarios derived from the virtual model and risk analysis simulation are used to understand where risks reside in the system and provide visualization of where security measures should be implemented with highest priority. Examined security measures are input to the virtual model to enable simulation of the risk mitigation effects as a result of implementing the measures. Many combinations of measures can be tested beforehand in the virtual model to enable development of economic and effective measures.
Fig 3: Simulation of security measures
- ※The information posted on this page is the information at the time of publication.

 NEC Technical Journal "An Analysis of the Actual Status of Recent Cyber attacks on Critical Infrastructures"
NEC Technical Journal "An Analysis of the Actual Status of Recent Cyber attacks on Critical Infrastructures"